 SmartPhone Enabled Mobile Health System
SmartPhone Enabled Mobile Health System
 Resilient Context-Aware Smartgrid Communication Network (RECAST)
Resilient Context-Aware Smartgrid Communication Network (RECAST)
 Secure Mobile Information Sharing (NSF funded Project):
SEMOIS
Secure Mobile Information Sharing (NSF funded Project):
SEMOIS
 Secure Efficient Content Centric Mobile
Networks(NSF funded Project): SECON
Secure Efficient Content Centric Mobile
Networks(NSF funded Project): SECON
 Assistive Technologies for Elderly and Disabled People
Assistive Technologies for Elderly and Disabled People
 Networked Enabled Robotic Assistive Technology for Independent Living - joint project with Prof J. Spletzer
Networked Enabled Robotic Assistive Technology for Independent Living - joint project with Prof J. Spletzer
 Secure Information Retrieval for Extreme Networks (SIREN)
Secure Information Retrieval for Extreme Networks (SIREN)
 Related Project -
A Million People Project at University of Cambridge
Related Project -
A Million People Project at University of Cambridge
 Adhoc/Sensor Network Technologies
Adhoc/Sensor Network Technologies
 Interdomain adhoc routing protocol
Interdomain adhoc routing protocol
 Security Design for Adhoc Networks
Security Design for Adhoc Networks
Endorse - DoS resilience for adhoc networks
 SRED-VAN - Secure Robust Efficient Delivery for Vehicular Adhoc Networks
SRED-VAN - Secure Robust Efficient Delivery for Vehicular Adhoc Networks
In this project, we design efficient delivery protocols for different vehicular applications e.g. delivering emergency medical information via roadside entities, traffic congestion monitoring. We also intend to explore security solutions for VANET.
Selected Publications
Completed Projects:
 Intelligent Message Filtering System for RADICAL (ARL funded Project):
IMF
Intelligent Message Filtering System for RADICAL (ARL funded Project):
IMF
 Disruption Tolerant Network (DTN) (DARPA funded Project):
EDIFY
Disruption Tolerant Network (DTN) (DARPA funded Project):
EDIFY
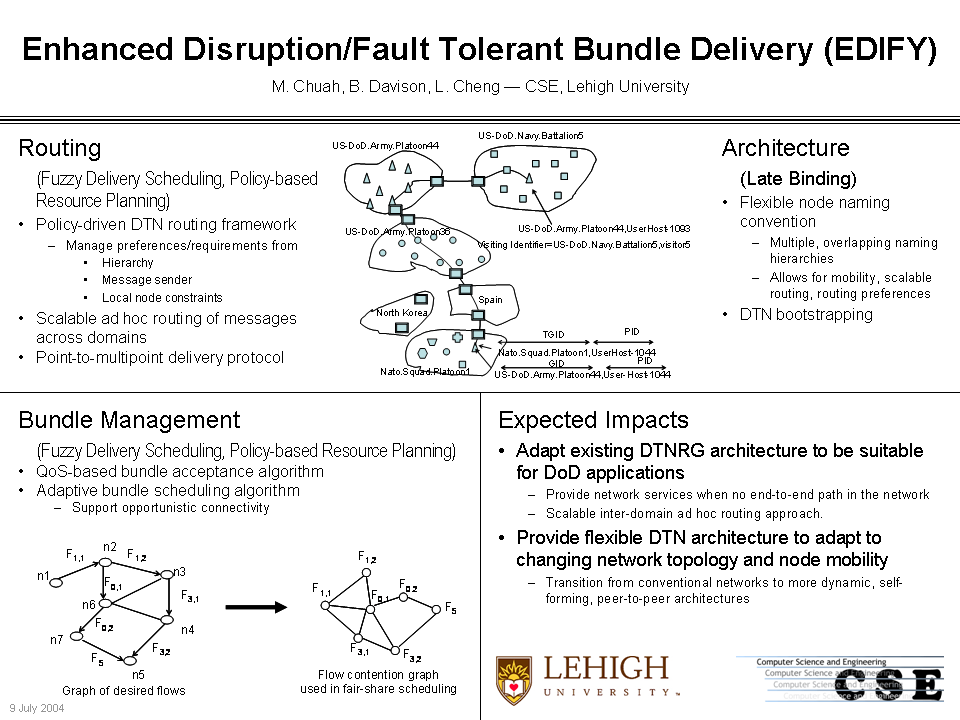 |
For more information on EDIFY , click here
Conference/Journal Publications for EDIFY project
 Anomaly Detection and Mitigation for Interdomain Routing
Exchanges (ADMIRE)
Anomaly Detection and Mitigation for Interdomain Routing
Exchanges (ADMIRE)
Selected Publications
 Traffic Management in 3G Networks
Traffic Management in 3G Networks